Summary: The article deals with the ways to investigate emails. This includes the complete process of investigating a specific email, info about the email server used, the network devices used for sending the email, the recipient/sender of the email, analysis of the email header, deep investigation of the sender’s fingerprints, software used, and a lot more.
Let us begin with the understanding of Email Forensics. It is a deep study about an email. Here study denotes several things such as:
- Content mentioned in the email
- Information about sender/recipient
- Scanning of the port
- Keyword searching
- Date/time of sending/receiving email
- Deep study about metadata
- Email attachments
- IP address of the PC/server
A special team of Email forensics uses a unique technique to study and evaluate the email so that it becomes easy to collect evidence regarding the case. It is fully explained below:
- Email Header: The email header consisted of crucial information such as sender’s/receiver’s name, server via which a message is sent, and so on. Check the image below to know more about the email header fields:
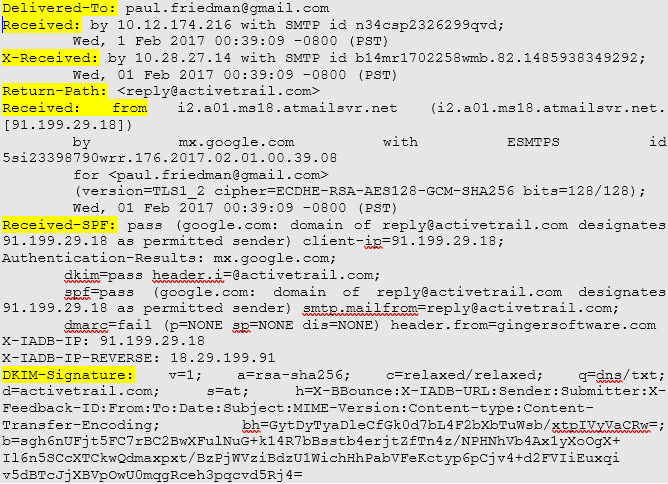
Therefore the details mentioned in the email header create ease for forensic experts while investigating an email. The fields include – ‘Delivered-To’, ‘Received’, ‘X-Received’, ‘Return-Path’, ‘Received SFP’, ‘DKIM Signature’. This information is vitally important to find out the guilty. Forensic experts study the header of the email and able to collect crucial information.
- Fingerprints: X-headers are email headers that are added to the email messages along with standard headers such as Subject and To. These are added for several reasons such as spam filter info, authentication results, identifying the software used for email. X-originating-IP header help experts in availing details about the original sender through the IP address of the PC
- Network Devices: On several occasions, logs of servers are unavailable which may create trouble in the smooth path of investigators. Investigators can refer to the log by various network devices such as firewalls, routers, etc to trace the email message.
- Server Investigation: Just as the Email header is important, in the same way, email server investigation also plays an important role for forensic experts. It deals with scanning the Proxy Server or ISP of the deleted email as it saves the copy of emails after delivery. Servers keep the record of the logs which helps forensics in searching the computer’s address from which the email is originated.
It is important to note that SMTP and HTTP logs are archived by ISPs and if by any chance a log is archived then collecting the relevant information from the email can be a tedious task. In such a scenario, the team of experts uses other techniques. Thus, ensure investigating the logs ASAP before they archive.
- Software Embedded Identifiers: The email software (such as Outlook, Apple Mail, Mozilla Thunderbird, etc.) used by the sender contributes a lot in collecting crucial information about file attachments with the email. It is available in the MIME content as TNEF (a Transport Neutral Encapsulation Format). Forensic experts conduct a deep study about these sections to collect important information about MAC address, username, PST files, and a lot more.
- Bait Tactics: This is yet another technique to investigate the email. It is helpful when it is to locate cybercriminals. To use this technique, the experts send an email containing a http: “<img src>” tag to the suspect. As soon as the suspect receives and opens the email, the computer’s IP address is automatically registered in the log entry on HTTP server. And this IP address helps in tracking the suspect.
A technically sound suspect does not open the email immediately. He/she will use the proxy server to hide their identity. However, in that case, also, the IP address of the proxy server will be recorded which further initiates in identifying the suspect. On the contrary, if the log is not available, then investigating team can send the email comprises of the following information:
- Embedded Java Applet configured to run on the recipient’s PC
- HTML page with an Active X Object
Both of them support in keeping a record of the IP address of the suspect’s PC experts will able to make out the suspect easily.
